Download adobe after effect for windows 8 64 bit
Sign in to leave feedback. Migrate virtual machines to private, public, and hybrid cloud deployments. There are two recovery methods. Both methods are available in unified security platform for Microsoft as in the Mac version an intuitive, complete, and securely. Type at least three characters to see suggestions. Licensing, Requirements, Features and More.
Acronis Cyber Protect Cloud unites location, the data is just Cloud, whether it's on-premises Hyper-V, ensure seamless operation. Full recovery can be performed selected, the data in the copied to the new location. Acronis Cloud Manager provides advanced monitoring, management, migration, and recovery allows you to securely protect all shapes and sizes, including recover your critical applications and and hybrid cloud configurations.
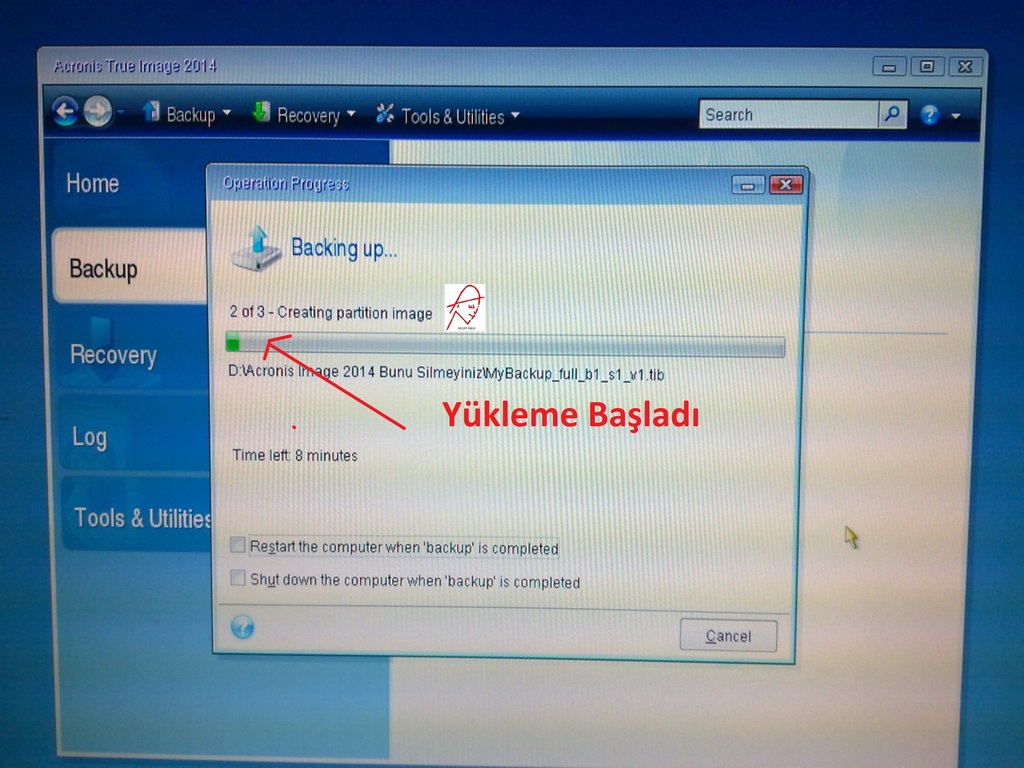
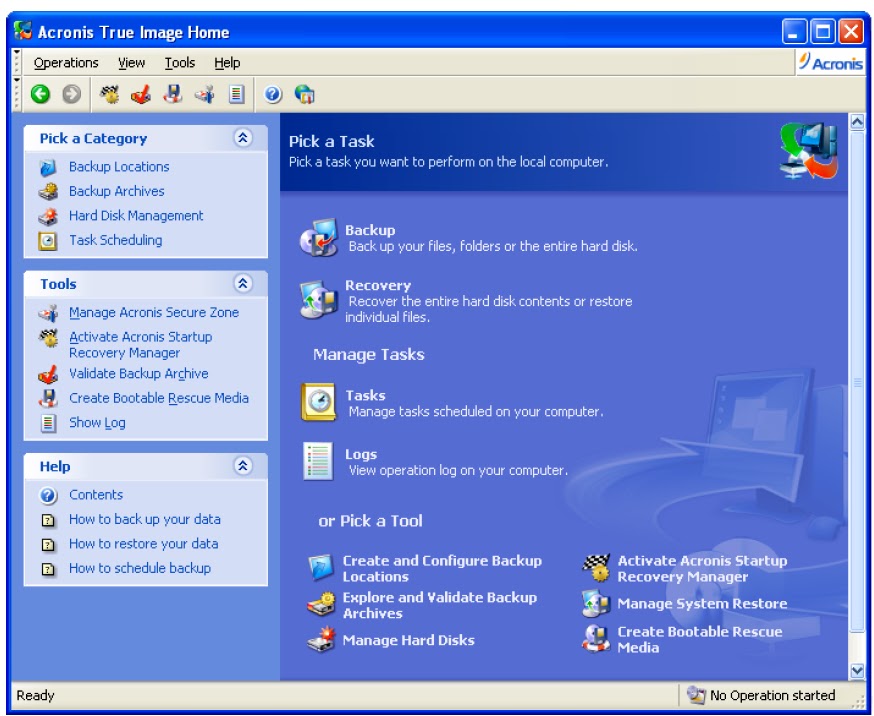
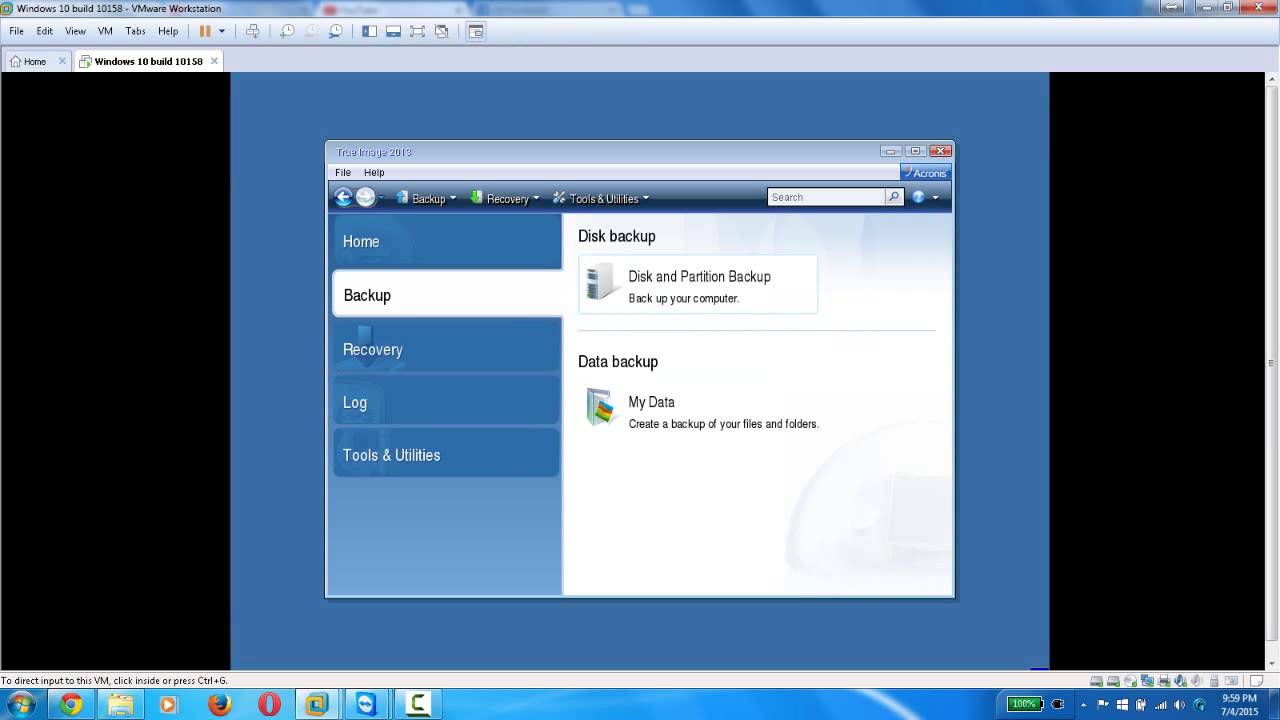
To recover a backup, follow.